ECW: Blog
8 Amazing Tips To Take Awesome Photos With Your iPhone
Smartphone technology and the internet have made it possible for us to share ideas—and do business—with people all over the world. Learning to use the powerful tools we have at our fingertips more effectively is one of the most significant…
Read MoreWhat Should Be In Your 2019 Technology Strategic Plan
Making an Ultimate Technology Plan for the New Year Times are changing. Apparently, this is the case considering we’re about to head into 2019. How is your current technology holding up at your company? If you feel like there are…
Read MoreHere’s How Cybercriminals Con Businesses In 2019
Is someone out there pretending to represent your business to make money? Don’t laugh. It happens. Business identity theft is a growing concern for many companies across the US. According to a recent study by Dun & Bradstreet, business identity theft, also…
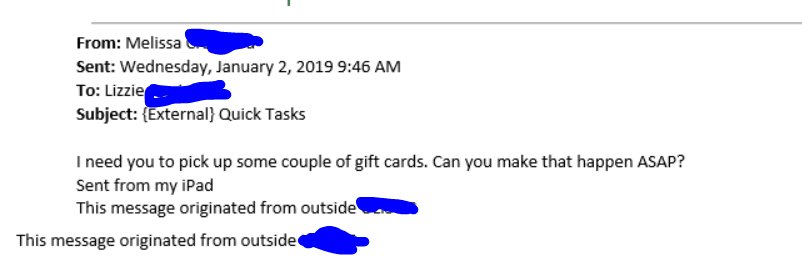
Read MoreSCAM ALERT: Google Play Gift Cards
If there’s a will there’s a way when it comes to scammers, especially with gift cards. Everyone loves gift cards. Consumers love how easy it is to purchase gift cards, use gift cards and even give gift cards. It’s as simple as…
Read MoreShould Your Business Upgrade It’s Website To WordPress 5.0.2
Only a few short weeks ago, we wrote about the introduction of WordPress 5.0 in early December and discussed whether or not your company should upgrade now, never or at a later date. Our recommendation was to wait until some…
Read MoreHow To Combat Cybercrime On A Small Business Budget?
If there’s one thing that most small businesses have in common, it’s a limited budget to invest in infrastructure. Yet failing to devote any resources to securing your technology can put the company itself at risk. Understanding the specific ways…
Read MoreHave You Heard Of This Scam Targeting Amazon Shoppers?
Amazon is a gigantic player in online sales. It’s estimated that the Seattle-based online e-commerce site will be responsible for roughly 50% of all digital sales during the 2018 holiday season, one of the busiest shopping times of the year…
Read MoreWho Provides Business Computer Services In Sunrise, FL?
See how ECW Computers delivers exceptional IT support for Sunrise FL businesses, including cloud computing, managed IT, data backups, consulting and security
Read MoreThe 2019 Cyber Security Guide For Financial Professionals
The securities industry has been as vulnerable to cyber attacks in 2018 as any other industry. According to the SEC’s Enforcement Division newly created Cyber Unit (formed in 2017 to enhance the ability of the Commission to identify and investigate…
Read MoreWhat Is The Microsoft 365 Freelance Toolkit
[youtube https://www.youtube.com/watch?v=PHUrEtCgNZ8]Companies today are increasingly relying on freelancers to support one-time or ongoing projects. The growing need for freelance support can create complex challenges for companies. How, for example, can companies manage projects across time zones? How can freelance and…
Read MoreRecent Posts
How can we help?
Whether you need immediate help with an IT issue or want to discuss your long-term IT strategy, our team is here to help.
Call us at (561) 303-2310 or complete the form below and we'll help in any way we can.
"*" indicates required fields