ECW: Blog
8 Intruder-Hating Tips For Home Office Security
Your Devices Are A Target For Online Prowlers. At Your Peril Do Not Ignore! Be Aware of Your Surroundings – Takes On a Whole New Meaning When you were a child, your mom or dad reminded you, be aware of…
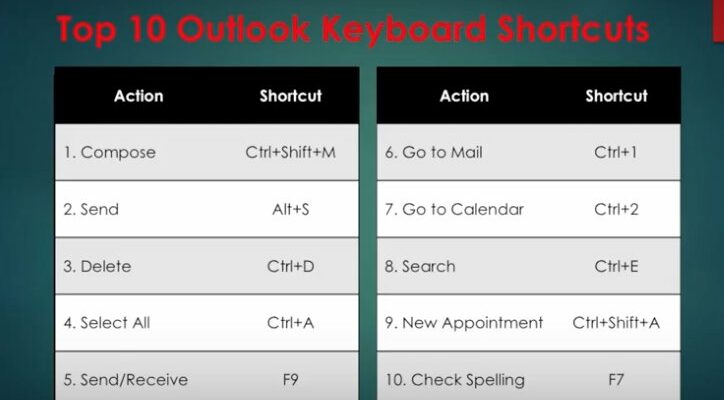
Read MoreIf You Don’t Know About These 3 Ways to Use Outlook 2016 More Efficiently, You’re Wasting Lots of Time
Microsoft Outlook is a professional email and calendar program that’s been used by businesses for over 15 years. It’s had many iterations over the years, but with 2016, and its integration with Office 365, Microsoft has taken Outlook to the…
Read MoreThe Latest Expansions To Microsoft Office 365 Will WOW You!
Tools used by top-notch Managed IT Services providers. The wildly popular subscription-based Microsoft Office 365 offers an ever-expanding application gallery. The latest additions to the line-up are sure to excite professional users. The professional landscape today appears quite different from…
Read MoreThe Top 12 Time Management Apps and Tools
Today’s app market offers the full range of apps for personal use and for work. Everyone seems to be trying to complete household chores and tasks at work with the highest level of efficiency. Time has become a valuable commodity…
Read MoreWant Your World At Your Fingertips In Just One Simple Step? You Got It!
The digital revolution has changed our world in unimaginable ways – and for the better! Tools and applications like Microsoft Word and Microsoft OneNote aim to make our lives easier, in one simple step. [youtube https://www.youtube.com/watch?v=-0Gb0ATRWS0]Have you ever stopped to…
Read MoreCalling All Architects
Do You Want to Save Time, Money and Beat Out the Competition? We Have Some Important Information to Share As you know, your architecture company is under constant pressure from economic shifts, a shrinking talent pool, and a fiercely competitive…
Read MoreAre We Learning Anything From All These Cyber Attacks?
So many big, expensive cyber attacks have taken place in the last few years that it’s hard to remember them all – when will we learn our lesson? Cyber attacks are common ground these days. There was the Chase Bank…
Read MoreTired of Sending Marketing Emails That Go in the “Trash”?
Here Are The 10 Things You’re Doing Wrong Email is a very effective marketing tool. However, it’s also tough to execute properly. If you don’t plan correctly, understand what you’re doing wrong and how to remedy this, you’re simply wasting…
Read MoreSemper Fi: Never Negotiate With Cyberterrorists
Another case highlighting the importance of Cybersecurity and Managed IT Services. A recent report by the U.S. Marine Corps indicates an unintended data disclosure, the result of a single accidental keystroke. Never backing down from a fight, learn from Jarheads…
Read MoreFrom Unaware Interns To Evil Executives: How To Say Sayonara With Skill
It’s never easy to terminate an employee. The skill of firing with flair is a sensitive but necessary process that everyone should learn! It happens to the best of us. We post an advertisement for an available position on job…
Read MoreRecent Posts
How can we help?
Whether you need immediate help with an IT issue or want to discuss your long-term IT strategy, our team is here to help.
Call us at (561) 303-2310 or complete the form below and we'll help in any way we can.
"*" indicates required fields